In Public Preview at the time of the writing. This is a much-needed feature I believe. Also in most of the IT departments due to the tasks being segregated among different admins, most of the time it is a team game and you need 2 different admins (Intune Administrator and a Security Administrator) to collaborate in finding the device policy details. And before this feature, there was no way to properly see the setup for the devices that are onboarded into MDE but not enrolled in Intune.
Some previous writing 👇🏽
Current (soon to be Previous) Experience
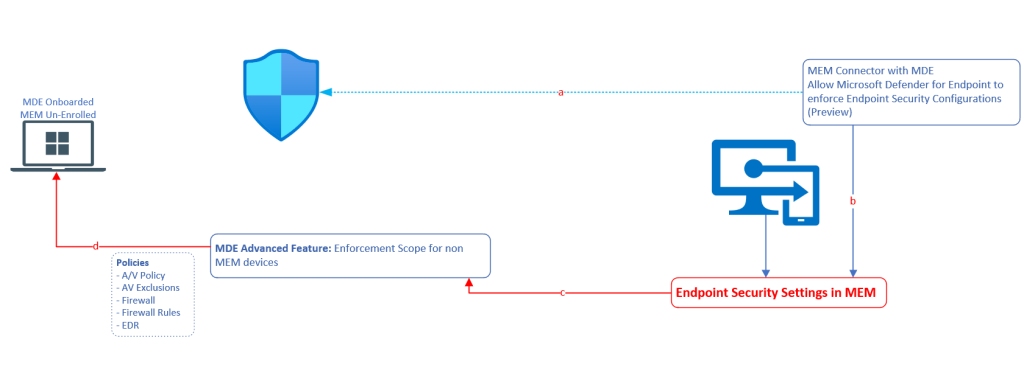
And that was configured from the below setting.
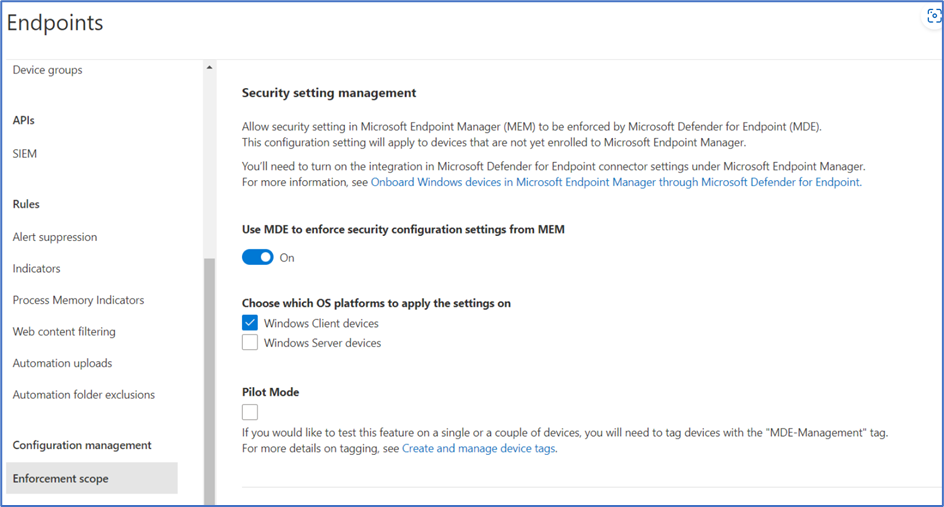
To add to the current experience,
- You use the Microsoft Intune admin center to configure endpoint security policies for Defender for Endpoint and assign those policies to Azure AD groups
- Devices get the policies based on their Azure Active Directory device object. A device that isn’t already present in Azure Active Directory is joined as part of this solution
- When a device receives a policy, the Defender for Endpoint components on the device enforces the policy and reports on the device’s status. The device’s status is available in the Microsoft Intune admin center.
New Experience
When you manage devices through security settings management as part of the public preview:
- You can use the Microsoft Intune admin center or the Microsoft 365 Defender portal to configure endpoint security policies for Defender for Endpoint and assign those policies to Azure Active Directory (Azure AD) groups. The Defender portal includes the user interface for device views, policy management, and reports for security settings management.
- Devices get their assigned policies based on their Azure AD device object. A device that isn’t already registered in Azure Active Directory is joined as part of this solution.
- When a device receives a policy, the Defender for Endpoint components on the device enforces the policy and reports on the device’s status. The device’s status is available in the Microsoft Intune admin center and the Microsoft 365 Defender portal.
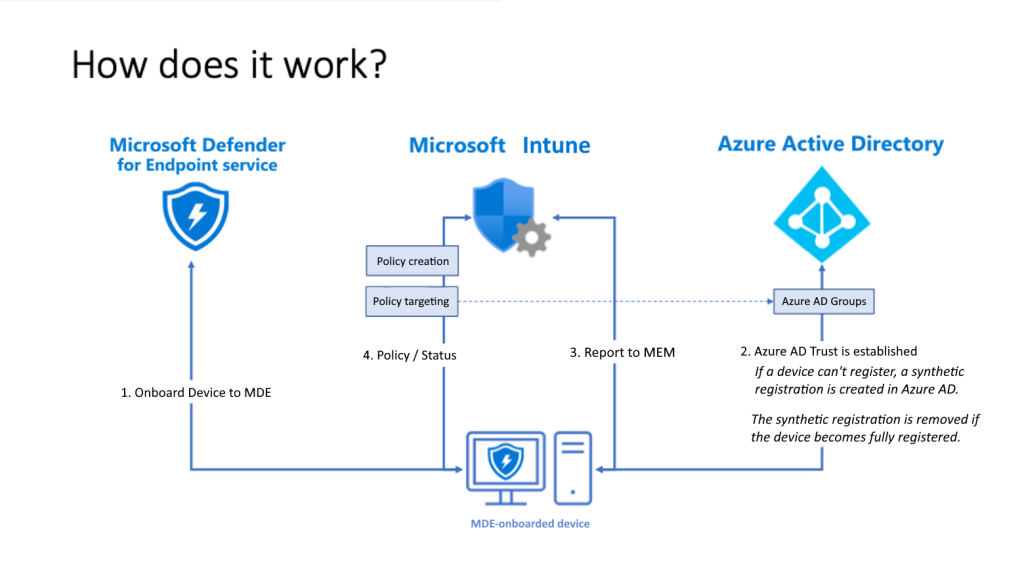
How this can help in better Device Management?
- This option now extends the devices that are not able to enroll in Intune.
- If the device is enrolled in Intune, then the Security policies will be managed by the Endpoint Security section.
Architecture
- Devices onboard to Microsoft Defender for Endpoint.
- A registration is established for each device in Azure AD:
- If a device has an existing trust, that trust is used.
- For devices that haven’t been registered, a synthetic device identity is created in Azure AD to enable the device to retrieve policies. When a device with a synthetic registration has a full Azure AD registration created for it, the synthetic registration is removed and the devices management continues on uninterrupted by using the full registration.
- For devices that were previously fully registered, like a Hybrid Join device, the existing registration is used.
- Devices use their Azure AD Identity to communicate with Intune. This identity enables Microsoft Intune to distribute policies that are targeted to the devices when they check-in.
- Defender for Endpoint reports the status of the policy back to Microsoft Intune.
Endpoints that need to be enabled from the device
enterpriseregistration.windows.net– For Azure AD registration.login.microsoftonline.com– For Azure AD registration.*.dm.microsoft.com– The use of a wildcard supports the cloud-service endpoints that are used for enrollment, check-in, and reporting, and which can change as the service scales.
Applies to
- Linux
- macOS
- Windows 10
- Windows 11
The Process
When a supported device onboards into Microsoft Defender for Endpoint:
- The device is surveyed for an existing Microsoft Intune presence, which is a mobile device management (MDM) enrollment to Intune.
- Devices without an Intune presence enable the security settings management feature.
- For devices that aren’t fully Azure AD registered, a synthetic device identity is created in Azure AD that allows the device to retrieve policies. Fully registered devices use their current registration.
- Policies retrieved from Microsoft Intune are enforced on the device by Microsoft Defender for Endpoint.
Active Directory Requirements
- Hybrid AAD Joined needs to be setup
- Device objects to be in the sync scope
- Azure AD Connect rules for sync must be modified for Server 2012 R2 (when support for Server 2012 R2 is needed).
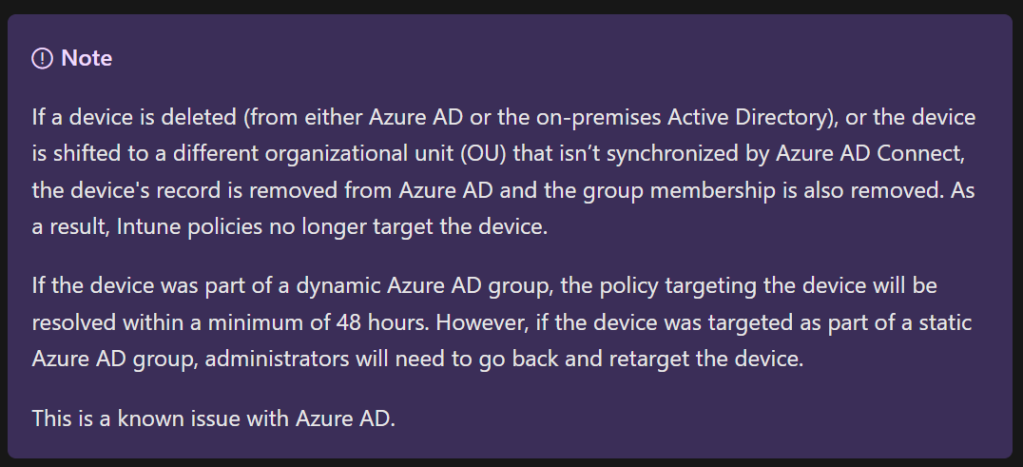
- All devices must register in the Azure Active Directory of the tenant that hosts Microsoft Defender for Endpoint. Cross-tenant scenarios aren’t supported.
Licensing and subscriptions
A subscription that grants licenses for Microsoft Defender for Endpoint, like Microsoft 365, or a standalone license for only Microsoft Defender for Endpoint.
🔗More on Licensing can be found here
Which method to use?

How to Configure Defender for Endpoint for these features?
To enable the feature for the devices there are two things to be fulfilled.
- Configuration of the Defender for Endpoint section of the Defender Portal
- Intune Portal configuration
Defender for Endpoint Configuration
https://security.microsoft.com > Advanced Features > Configuration Management > Enforcement Scope >
Enable –> Use MDE to enforce security configuration settings from Intune
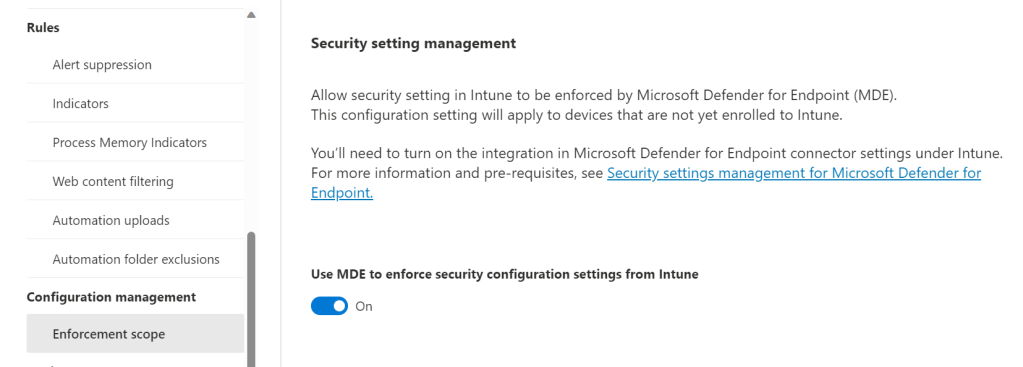
Select the platforms

ON –> Security settings management for Microsoft Defender for Cloud onboarded devices.
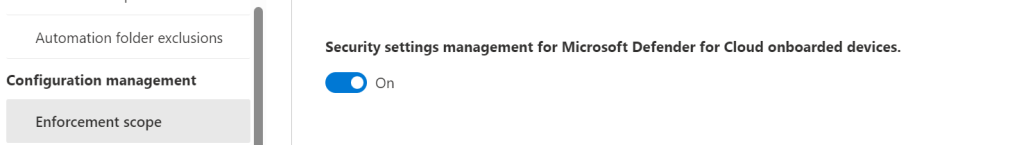
Configure Intune
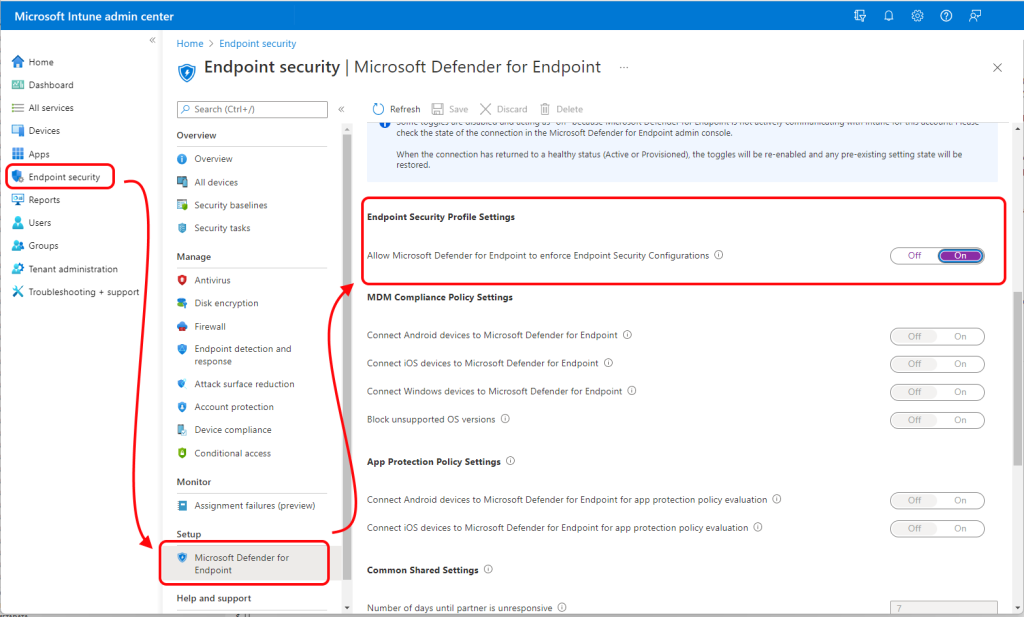
Go to intune.microsoft.com > Select Endpoint security > Microsoft Defender for Endpoint, and set Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations to On.
What to Expect in the Security Portal?
If you go to the Endpoints section, you will see the Configuration Management section and subsections, Dashboard, and Endpoint security policies
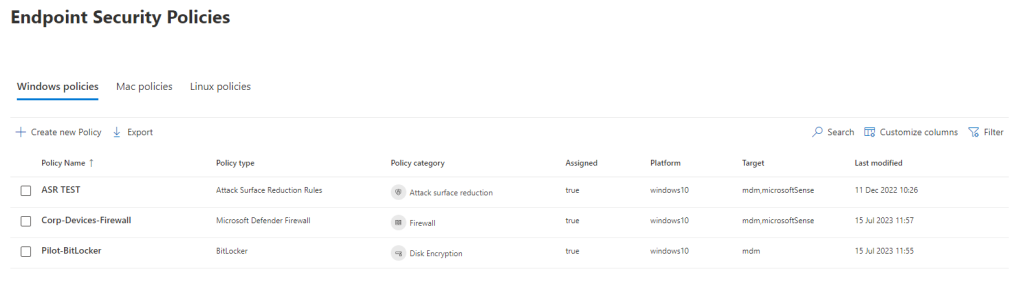
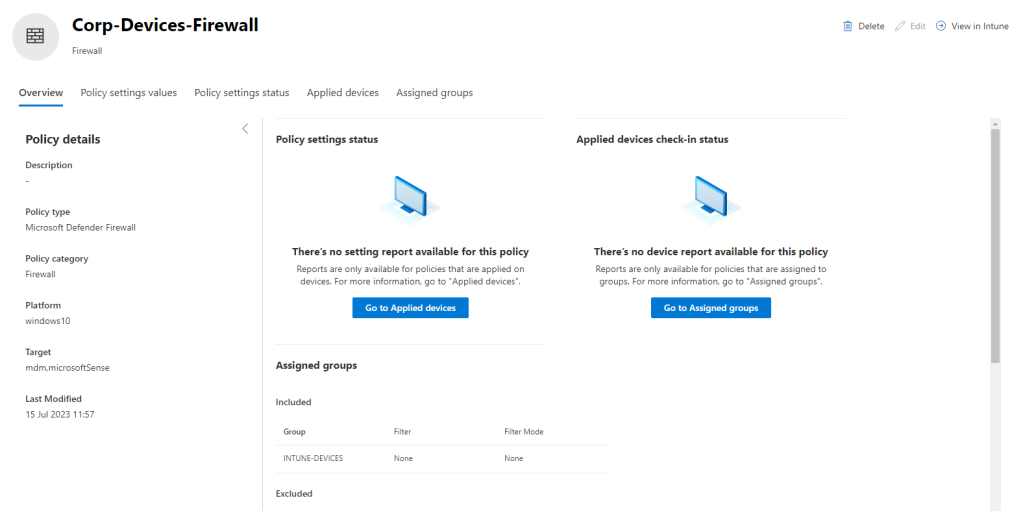
From the device, go to Security Policies to see all the available policies assigned to the device

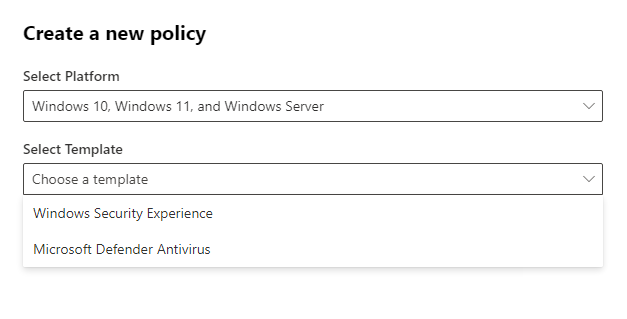
At the time of writing, only Defender A/V and Windows Security Experience Policy templates are available to create from the Defender portal
Device Check-in Frequency
The standard policy sync time is 90 minutes.
You can manually sync a device on-demand from the M365 Defender Portal Sign-in to the portal and go to Devices. Select a device that is managed by Microsoft Defender for Endpoint, and then select the Policy sync button.
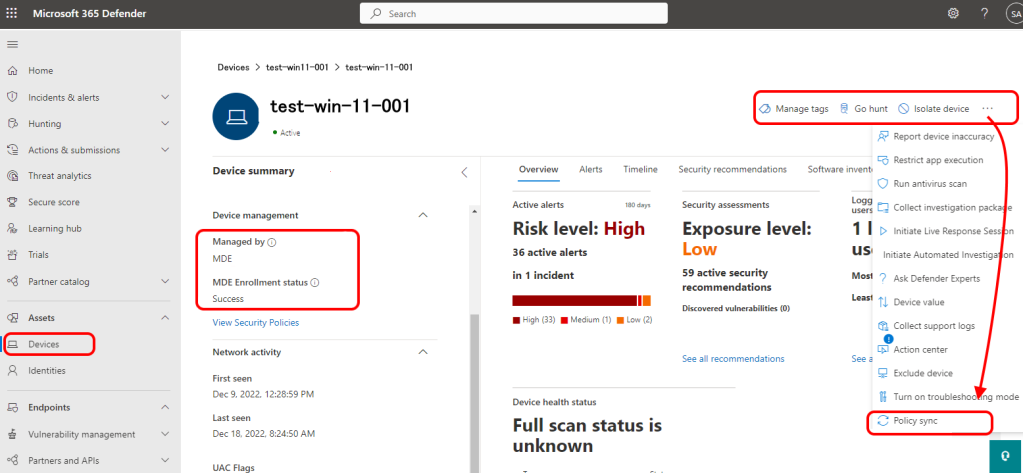
The Policy sync button only appears for devices that are successfully managed by Microsoft Defender for Endpoint.
🔗Some important notes on the settings
Wrapping Up
This is hands down a great step towards better and more efficient device management. And most of all, this simplifies the management. Looking forward to seeing more Endpoint Security related features in the Defender Portal.
Discover more from EMS Route
Subscribe to get the latest posts to your email.

Thank you for the write up. Can there be a situation where a MDE and MEM security setting would be in conflict? If so, who wins?
LikeLike
Hi Michael,
Thanks for your message. It will not be in conflict. Because the policy you create in MDE will be synchronized to Intune and visa-versa. The device groups will be reflected in the same way so there will be no conflict. However, there are some options like device filters, scope tags you will have to go to the Intune portal.
Hope this helps.
LikeLike
Hi, do you know if the new experience supports Windows servers? Specifically the part with the synthetic AAD registration. If that is supported for Windows servers, then wouldn’t that mean that we could drop the whole AD-Connect sync of server objects, to achieve hybrid join? Just onboard them to Defender either manually or using Azure Arc, and then be able to configure policies via Intune.
LikeLike
Hi Benjamin,
AAD Join only supports Windows 10/11 at the moment. Also, even though the device is onboarded to Defender, the Security policy assignments are managed by Entra ID. This means the device should be Hybrid AAD Joined which requires the AAD Connect Sync.
This new way of managing the devices using the Defender portal is making the device management easy so the admins won’t have to move between portals and all things Security policies should be able to be managed in the Defender portal. Hope this is helpful.
Shehan.
LikeLike