The perfect Azure AD, Intune combo does not exi…..
Some time ago I wrote about Azure AD PIM for groups and its usages. This came to light a few days ago in Microsoft Tech Community as an article and I thought I will give my touch to it.
What is it and Why Does This Matter?
As you know Intune Administrator role can be configured with the Azure AD PIM features, but if you need to configure PIM features for the in-built roles in Intune it will be an issue because it’s not available there.
This is why it’s definitely going to be a very good use case for combining the power of Azure AD PIM with the Intune RBAC we know.
The concept is simple to understand. Azure AD role Intune Administrator can be PIM’ed and that has the highest access level for the Intune tenant.
What’s lacking in Intune’s built RBAC?
And in most cases, Intune’s in-built RBAC settings are used to create different access levels for the admins because not every admin doesn’t need to ba an Intune Administrator. Starting from Level 1 to Level 3, Contractors, Admins who need access only to a specific section of Intune and etc. But once the admin is in the group,
- Access is not time-bound access
- Access is permanent and not as needed basis
- No strong authentication methods are available
- Access reviewed
The Missing Link
Azure AD Groups for PIM is so perfect as it fits right into the above points to combine everything and strengthen your Identity game.
Licensing Requirements
Azure AD Premium P2 to use PIM features
How to Use This?
Create your Azure AD Group with the PIM for groups feature enabled.
Create your Intune in-built role by login to the Intune portal > Tenant administration > Roles
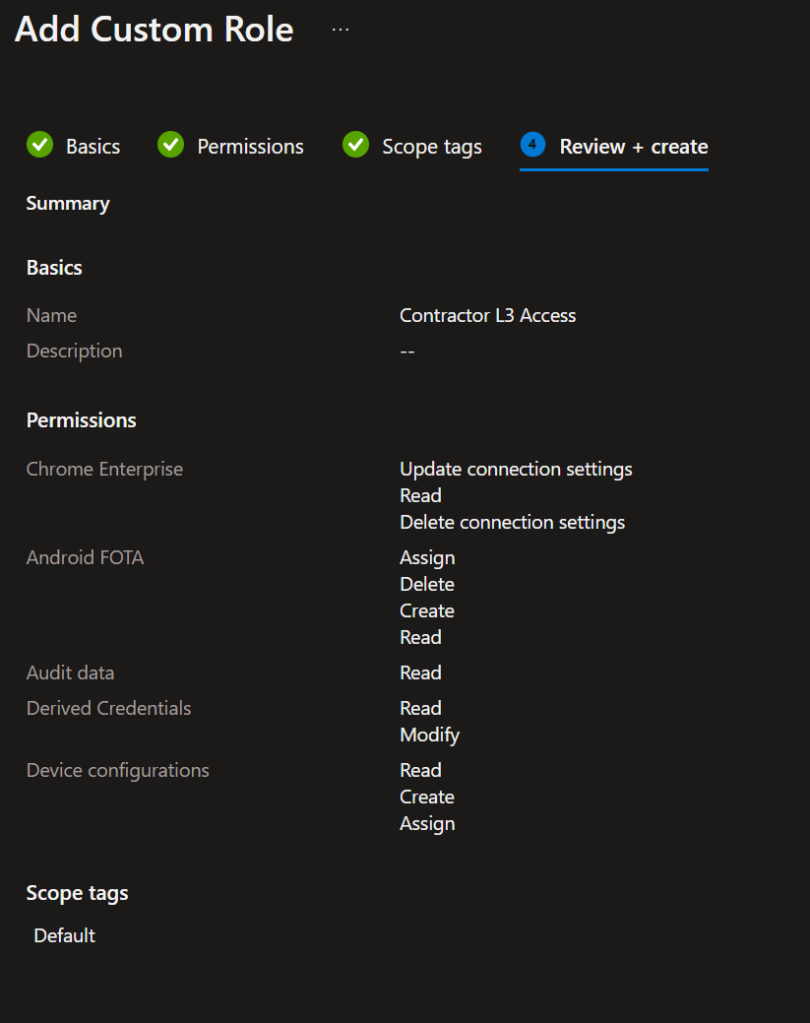
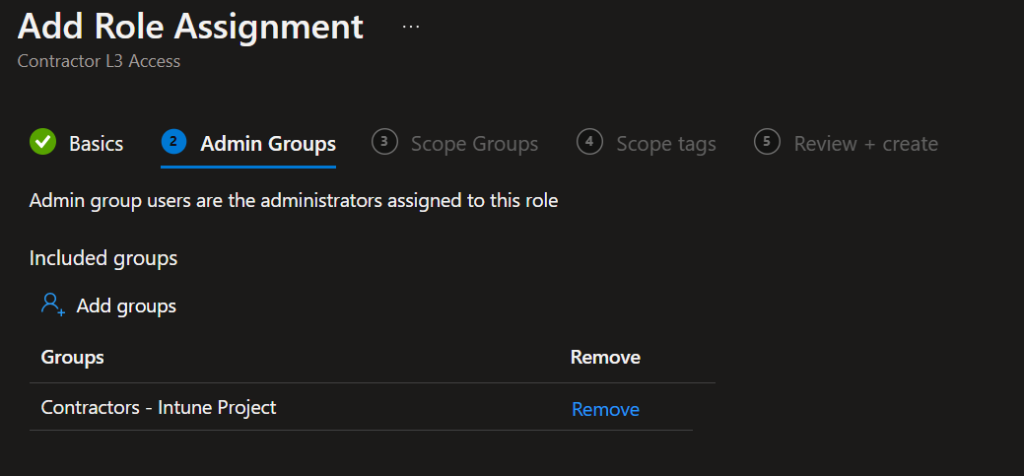
Assign the above created Role to the group and select the AAD Group for PIM enabled group from Step 1
Intune portal > Tenant administration > Roles > Select the role > Assignments > Assign

Add the group
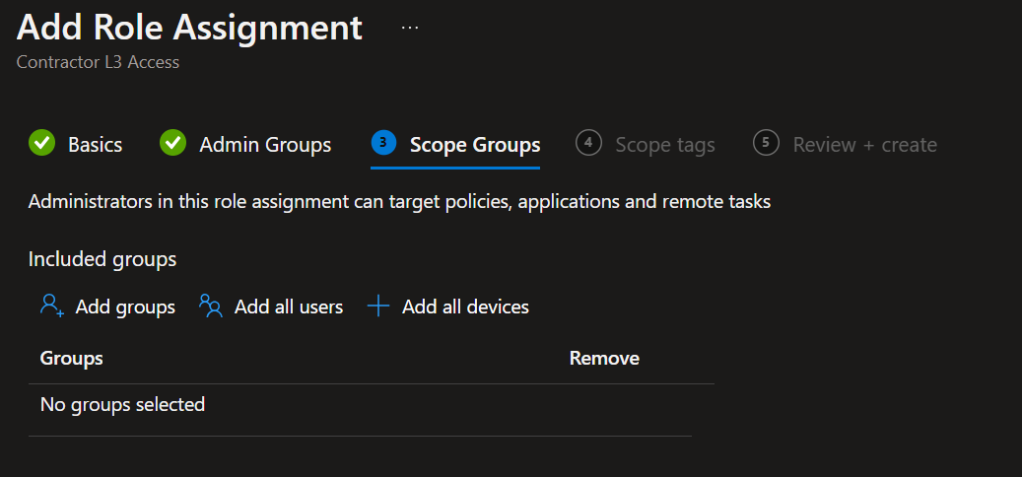
Set up the Scope Groups and add the selected users and devices groups or add All Users and All Devices so the assigned admins can see them accordingly.
Add Scope tags if needed.
Review and Save.
End Result
Now that we’ve added the Azure AD for PIM activated group, the members in the group will be Just In Time-based and will get the rich features of Azure AD PIM.
Eligible Role admin will now go to aka.ms/pimg and will see their eligible groups. When Activating, the PIM settings come into play. Justifications, Completion of Strong Auth, Ticket details, and going through someone who can accept the elevation request, before being a member of the group.
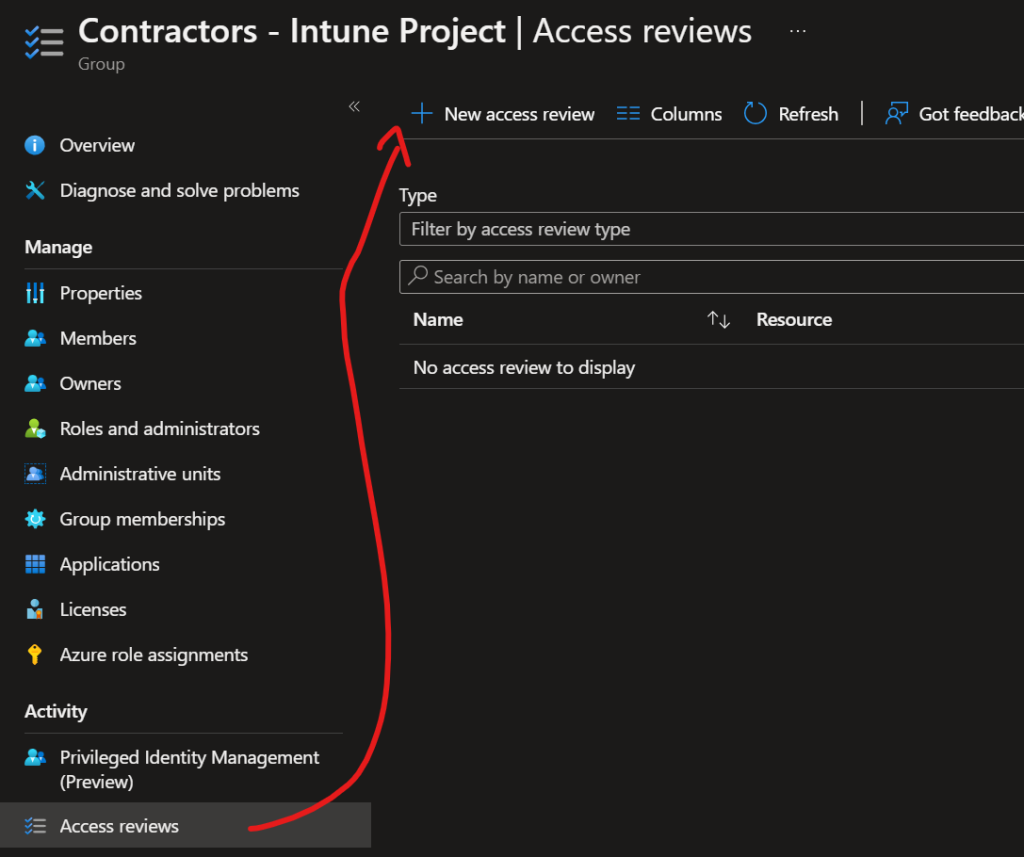
Set Access Reviews for the Assignment Group (optional)
This is a great way to be on top of the access. If you have longer access windows, best to use Access Reviews as well so the memberships will be re-evaluated.
Wrapping Up
Giving the AAD Groups for PIM touch to Intune In-built roles is a wise decision as any unmanaged access to a critical system like Intune can be harmful. By unmanaged I meant – you assign the group to the role and never go back to check who are the users, who needs to go out of the group, and no special method to authenticate.
On a closing note, I really believe the PIM features will be built into the Roles one day – But this is just my thought.
Discover more from EMS Route
Subscribe to get the latest posts to your email.

One thought on “Configure Intune Built-In Roles Using Azure AD PIM for Groups”