The easiest step in any policy creation. Yet there is a possibility that the policy assignment to end up with errors. I want to discuss that in this article.
We have our policy created with all the settings and we are pretty happy with it. The next step is assigning it to one of the options from All Users, All Devices, or to a selected Group/s. Same as setting up exclusions if needed. Of course, we know our target device or user groups, and it’s very easy to add those groups under Assignment. So what can go wrong?
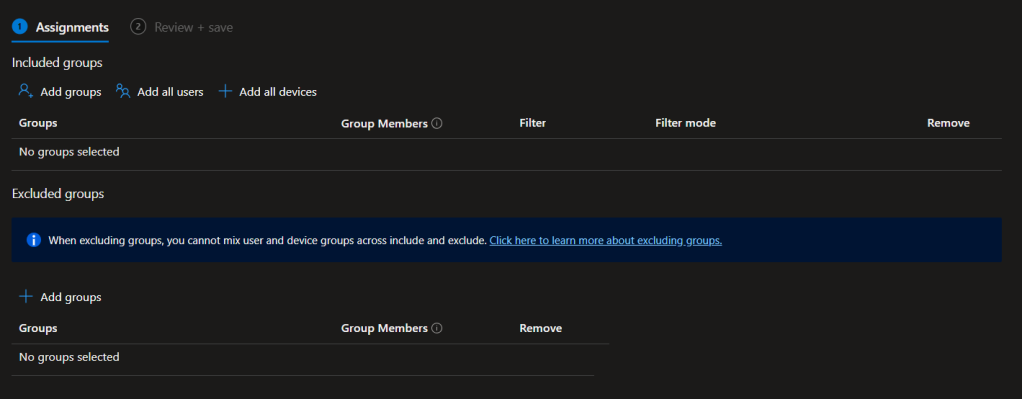
Right off the bat, as you can see above, there is an information strip coming up when you go to the assignments section. When excluding groups, you cannot mix user and device groups across include and exclude.
What does this really mean? You can’t exclude the same device or user that you already had in include? or you can’t have users and devices in the same group to include and exclude? it was a bit confusing for me at 1st.
We don’t want to worry about this up to some extent as long as we do includes only. The confusion comes when we need to exclude.
When to use Device Groups? When to use User groups?
It comes down to your policy end goal. This is similar to GPOs.
User Groups – If you need to apply the policy to users so that whenever they log in to a managed device, the policy will apply
Device Groups – Policy will be applied to any managed device regardless of the logged-on user
Note that when you try to create policies, there are some policies that are specific to either Users or Devices. At that time, the exact group should be selected.
Removing a Device or User Groups Won’t Really Undo the Changes…..Sometimes
Let’s understand why this is happening like that. The policy settings are based on the CSPs (Configuration Service Providers) and these settings will configure different parts of the Windows device depending on the policy you create.
These settings behave in different ways. Some settings will go back to the original state when the removal or added to the exclusions at a later stage.
Some settings, once they are configured, it will not go back to their original state. Or you can think it as the tattooing effect of the settings. This has been a bit of a worry sometime ago but a lot of tattooing settings are now undoing, yet there are settings that behave differently.
Sometimes the device needs a reboot to properly undo the setting.
From Microsoft Learn 👇🏽
To change a setting to a different value, create a new policy, configure the setting to Not Configured, and assign the policy. When the policy applies to the device, users should have control to change the setting to their preferred value.
Using Device Filters for User Group Assignments
This comes as a best practice when you need to assign policies to users and if you need to exclude some devices from the assignment. Device Filters can be used to exclude or include devices depending on the scenario. The principal behind this is user policy will be any managed device that the user is logging on to, but with a filter, you can specify not to get the policies to be assigned.
For more on the policies, check my previous blog below
Policy Assignment Principals
Microsoft has some principles to follow when including and excluding groups. I have added them straight from the MS Learn pages
- Think of Included groups or Excluded groups as a starting point for the users and devices that will receive your policies. The Azure AD group is the limiting group, so use the smallest group scope possible. Use filters to limit or refine your policy assignment.
- Assigned Azure AD groups, also known as static groups, can be added to Included groups or Excluded groups. Typically, you statically assign devices into an Azure AD group if they’re pre-registered in Azure AD, like with Windows Autopilot. Or, if you want to combine devices for a one-off, ad-hoc deployment. Otherwise, it might not be practical to statically assign devices into an Azure AD group.
- Dynamic Azure AD user groups can be added to Included groups or Excluded groups.
- Excluded groups can be groups with users or groups with devices.
- Dynamic Azure AD device groups can be added to Included groups. But, there can be latency when populating the dynamic group membership. In latency-sensitive scenarios, use filters to target specific devices, and assign your policies to user groups. For example, you want policies assigned to devices as soon as they enroll. In this latency-sensitive situation, create a filter to target the devices you want, and assign the policy with this filter to user groups. Don’t assign to device groups. In a userless scenario, create a filter to target the devices you want, and assign the policy with the filter to the “All devices” group.
- Avoid adding dynamic Azure AD device groups to Excluded groups. Latency in dynamic device group calculation at enrollment can cause undesirable results. For example, unwanted apps and policies might be deployed before the excluded group membership is populated.
Support Matrix
This may come in handy when you need to assign groups. This is again from the Microsoft Learn docs as it has a good explanation of the combinations.
- ✔️: Supported
- ❌: Not supported
- ❕ : Partially supported

| Scenario | Support |
|---|---|
| 1 | ❕ Partially supported Assigning policies to a dynamic device group while excluding another dynamic device group is supported. But, it’s not recommended in scenarios that are sensitive to latency. Any delay in exclude group membership calculation can cause policies to be offered to devices. In this scenario, we recommend using filters instead of dynamic device groups for excluding devices. For example, you have a device policy that’s assigned to All devices. Later, you have a requirement that new marketing devices don’t receive this policy. So, you create a dynamic device group called Marketing devices based on the enrollmentProfilename property (device.enrollmentProfileName -eq "Marketing_devices"). In the policy, you add the Marketing devices dynamic group as an excluded group.A new marketing device enrolls in Intune for the first time, and a new Azure AD device object is created. The dynamic grouping process puts the device into the Marketing devices group with a possible delayed calculation. At the same time, the device enrolls into Intune, and starts receiving all applicable policies. The Intune policy may be deployed before the device is put in the exclusion group. This behavior results in an unwanted policy (or app) being deployed to the Marketing devices group. As a result, it’s not recommended to use dynamic device groups for exclusions in latency sensitive scenarios. Instead, use filters. |
| 2 | ✔️ Supported Assigning a policy to a dynamic device group while excluding a static device group is supported. |
| 3 | ❌ Not supported Assigning a policy to a dynamic device group while excluding user groups (both dynamic and static) isn’t supported. Intune doesn’t evaluate user-to-device group relationships, and devices of the included users won’t be excluded. |
| 4 | ❌ Not supported Assigning a policy to a dynamic device group and excluding user groups (both dynamic and static) isn’t supported. Intune doesn’t evaluate user-to-device group relationships, and devices of the included users won’t be excluded. |
| 5 | ❕ Partially supported Assigning a policy to a static device group while excluding a dynamic device group is supported. But, it’s not recommended in scenarios that are sensitive to latency. Any delay in exclude group membership calculation can cause policies to be offered to devices. In this scenario, we recommend using filters instead of dynamic device groups for excluding devices. |
| 6 | ✔️ Supported Assigning a policy to a static device group and excluding a different static device group is supported. |
| 7 | ❌ Not supported Assigning a policy to a static device group and excluding user groups (both dynamic and static) isn’t supported. Intune doesn’t evaluate user-to-device group relationships, and devices of the included users won’t be excluded. |
| 8 | ❌ Not supported Assigning a policy to a static device group and excluding user groups (both dynamic and static) isn’t supported. Intune doesn’t evaluate user-to-device group relationships, and devices of the included users won’t be excluded. |
| 9 | ❌ Not supported Assigning a policy to a dynamic user group and excluding device groups (both dynamic and static) isn’t supported. |
| 10 | ❌ Not supported Assigning a policy to a dynamic user group and excluding device groups (both dynamic and static) isn’t supported. |
| 11 | ✔️ Supported Assigning a policy to a dynamic user group while excluding other user groups (both dynamic and static) is supported. |
| 12 | ✔️ Supported Assigning a policy to a dynamic user group while excluding other user groups (both dynamic and static) is supported. |
| 13 | ❌ Not supported Assigning a policy to a static user group while excluding device groups (both dynamic and static) isn’t supported. |
| 14 | ❌ Not supported Assigning a policy to a static user group while excluding device groups (both dynamic and static) isn’t supported. |
| 15 | ✔️ Supported Assigning a policy to a static user group while excluding other user groups (both dynamic and static) is supported. |
| 16 | ✔️ Supported Assigning a policy to a static user group while excluding other user groups (both dynamic and static) is supported. |
Wrapping up
Few things worth noting before wrapping up. Though this may seem a direct step, it involves understanding the assignment principles to create an error-free policy.
- Always start with a pilot group. If anything goes wrong, it’s easy to undo the policy
- Get to know the CSP locations you applying via the policies and if you need any manual intervention, you can easily navigate to it
- Understand when to use the device filters as they will come in handy
Discover more from EMS Route
Subscribe to get the latest posts to your email.

Hi there Shehan! This is a truly a really great blog post and I hope to see more like this!
I’ve got a question for you regarding your last comment in the “When to use Device Groups? When to use User groups?” section: “Note that when you try to create policies, there are some policies that are specific to either Users or Devices. At that time, the exact group should be selected.”
What’s the investigation process one needs to follow to determine if a given policy is specific to users or devices?
How would one go about figuring out if a settings in a Configuration Profile or AV policy or Disk encryption policy or ASR etc. are scoped to users or devices?
For example, if I’m creating a Device Compliance policy for Windows 10 & 11, I might head over to this article to learn more about each setting.
https://learn.microsoft.com/en-us/mem/intune/protect/compliance-policy-create-windows
Some settings on that page have a link to a CSP page like Require BitLocker, Encryption, Firewall etc. that contain more information indicating it only supports targeting Devices.
Some settings on that paege DO NOT have a link to a CSP page like many in the Password section, some settings in Defender, Defender for Endpoint, etc. So does that mean it doesn’t matter if it’s targeted to users or devices?
In the Password section you have to be extra careful as if you use a specific setting then you need to review those CSP pages to figure out if it’s applicable to users or devices or both.
But let’s say for a moment we have the information we need to take care of our Device Compliance policy. What about Configuration Profiles? Where’s the equivalent page that covers the various profile types that can be configured in Configuration profiles: Settings Catalog, Device restrictions, Administrative templates, Endpoint Protection etc.? What about the other policies that can be set under Endpoint Security?
Just hoping for some guidance to ease the burden of figuring things out.
IMHO: Microsoft should (a) highlight the scope of a setting in the page to make it super easy and (b) the moment you select a setting that is restricted to one scope (device or user) the settings for the opposite scopes are grayed out. This makes it much easier on the admin to sort out.
LikeLike
Nice article! Could you go into explaining the ”When excluding groups, you cannot mix user and device groups across include and exclude’ actually means? You said it was confusing but I don’t think the article explains what that actually means
LikeLike
Hi Damian,
Thank you. Technically, if you add users and devices in a mix, that will not give you the expected results. Mainly because there are policy settings that applies only to users or only to devices in some cases. Assigning it to a group that has both with the intention of excluding or including may give errors. Hope this doc will help you to understand this more. https://learn.microsoft.com/en-us/mem/intune/configuration/device-profile-assign#exclude-groups-from-a-profile-assignment
LikeLike
Thanks Shehan. Any idea what happens when you have a policy assigned to both “All users” AND “all devices” and then try to exclude a user/device from that policy? I feel the policy still applies even when you add the 2 separate exclusion groups (one for the user, one for their device). They still get the policy.
Do you have some quick tips on how you personally assign various configs? For example, ASR rules whether assigned to user or device. What’s best and when? My understanding is user assignment is the preferred but not sure if this applies to ASR rules, endpoint protection, etc too. It makes sense in a way, eg tech guys may need more loose ASR rules for whatever reason when they log in .
LikeLike